


Posted on July 25, 2025 | 9 min read
There is an increase in cybercrime, and the attackers are becoming more imaginative each day. Domain names that are registered and even altered by threat actors are behind most online scams, phishing sites, and malware networks. That is where WHOIS history comes in. Investigating the previous WHOIS records, such digital forensics specialists can reconstruct the domain registration history, the way it has changed over time, and other regularities that emerge in various malicious websites.
In this blog, we will explore how historical WHOIS data can be a powerful tool in cyber forensic analysis. You will learn what WHOIS history is, why it matters for cybercrime investigations, and how to use it step by step to uncover hidden connections between domains. Now let's get down to it. So, to begin with.
WHOIS is like a directory for domain names it tells you who registered a website, when they did it, along with the registration details and where they’re located. Every time someone registers or updates a domain, that information gets logged.
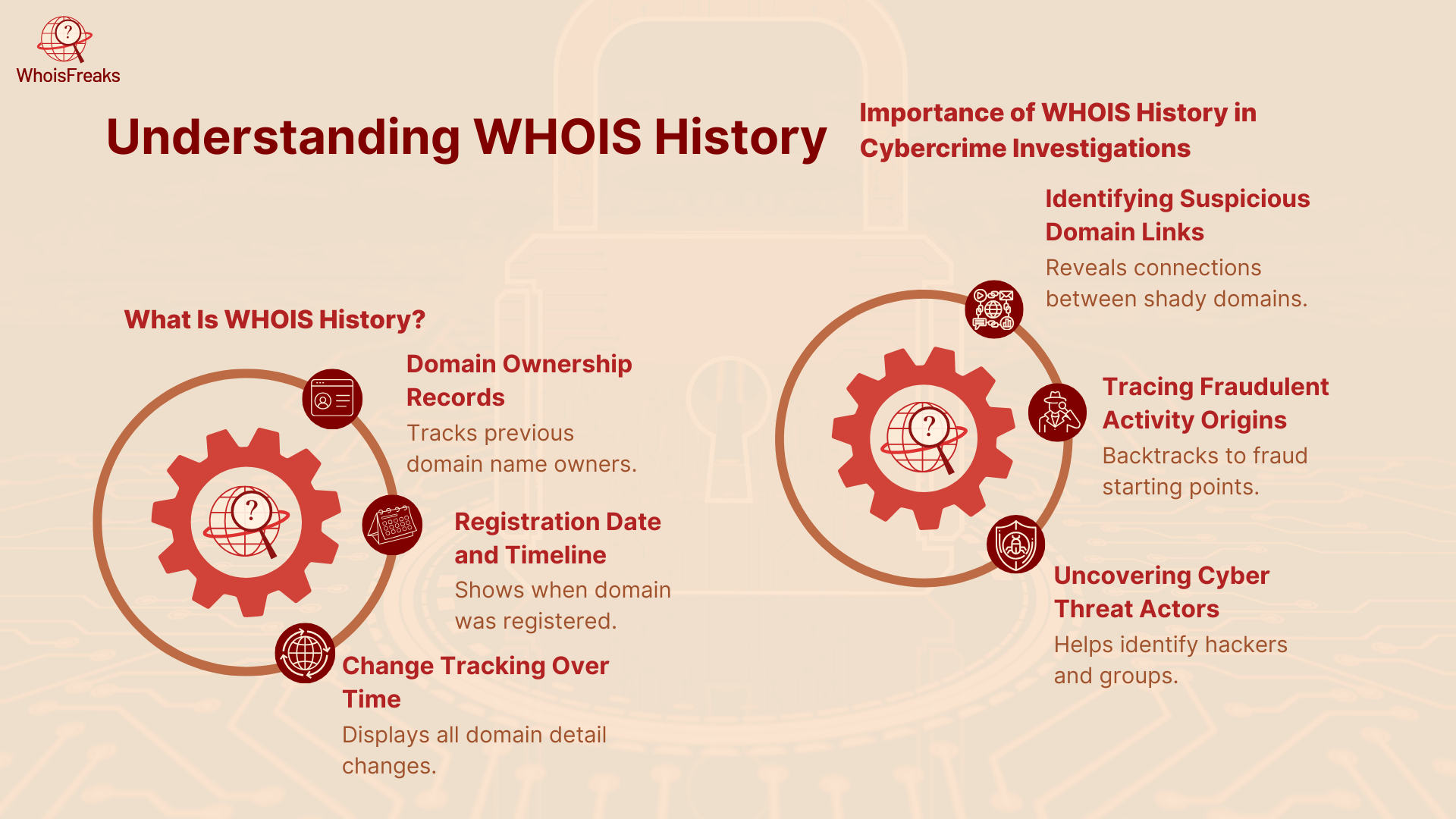
WHOIS history means looking back at those past logs to understand the domain history. Instead of just seeing today’s details, you can see how the domain record has changed over time. For example, you might discover that:
These snapshots of past WHOIS entries are kept by specialized services. They collect and store WHOIS data regularly, so you can pull up a timeline showing exactly when each change happened. This timeline helps investigators spot trends and data points like the same email showing up across multiple bad domains or sudden shifts used to hide a domain’s true owner.
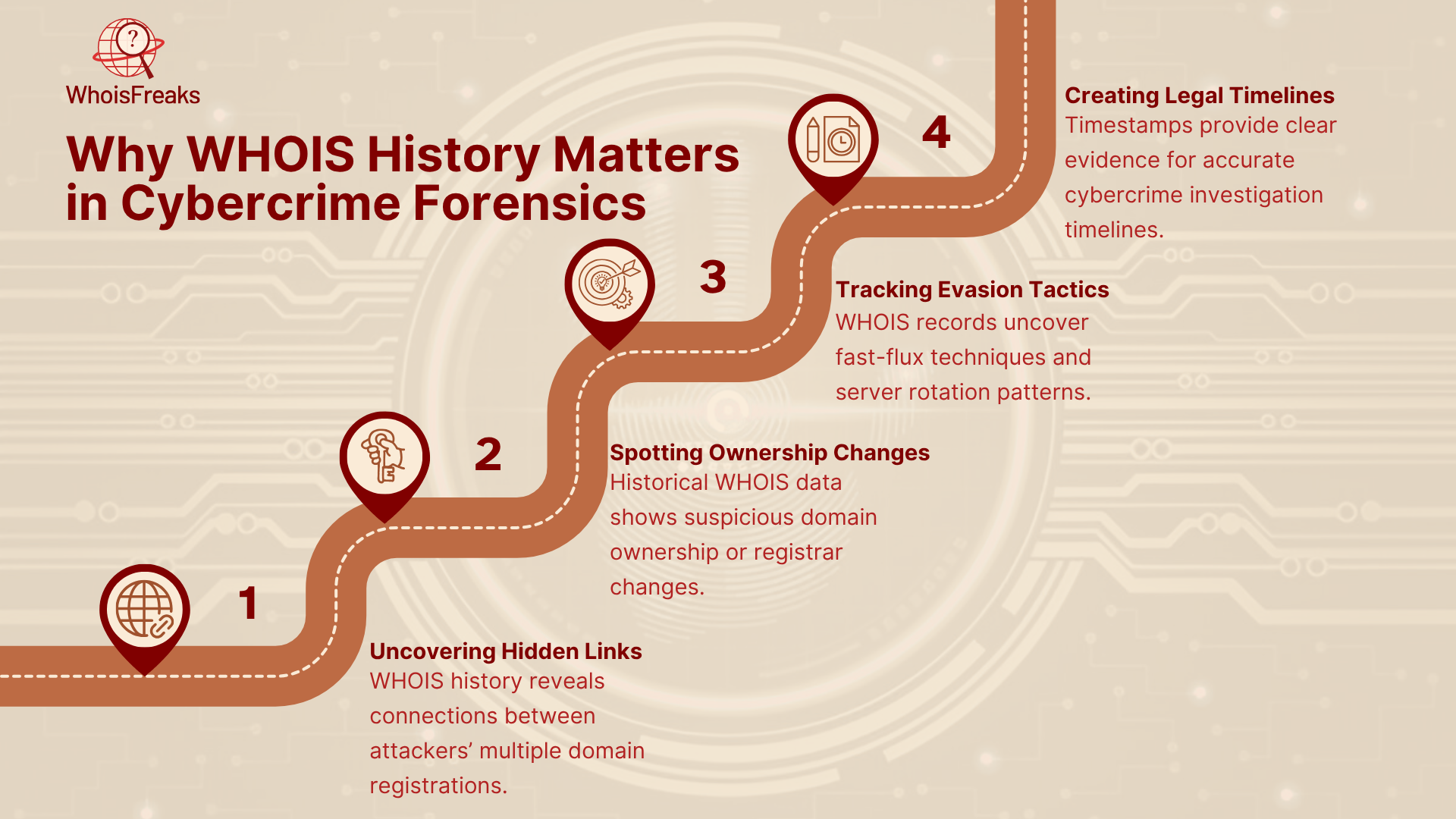
Cybercriminals also tend to open more malicious domains with the same email or name. Looking at the WHOIS history, you can also view whether registration information was shared by various domains at any time. This assists in tracing attacks that are separate to the same group.
Criminals can sell a domain to another party so that they are not being tracked. Red flag is an unexpected change on registrant name or registrar. Among the WHOIS records of the past one can find precisely when and how the ownership changed.
Attackers employ fast-flux (turnover of name servers often) or use large numbers of domains, to avoid takedown. WHOIS history records logs of name server changes, as well as registration dates, and you can see such quick steps and even guess what activity they will take next.
In legal cases, there should be clear evidence to show when a domain was in the control of crimes. WHOIS history keeps a record of the updates in the form of timestamps that make your report more accurate and powerful.
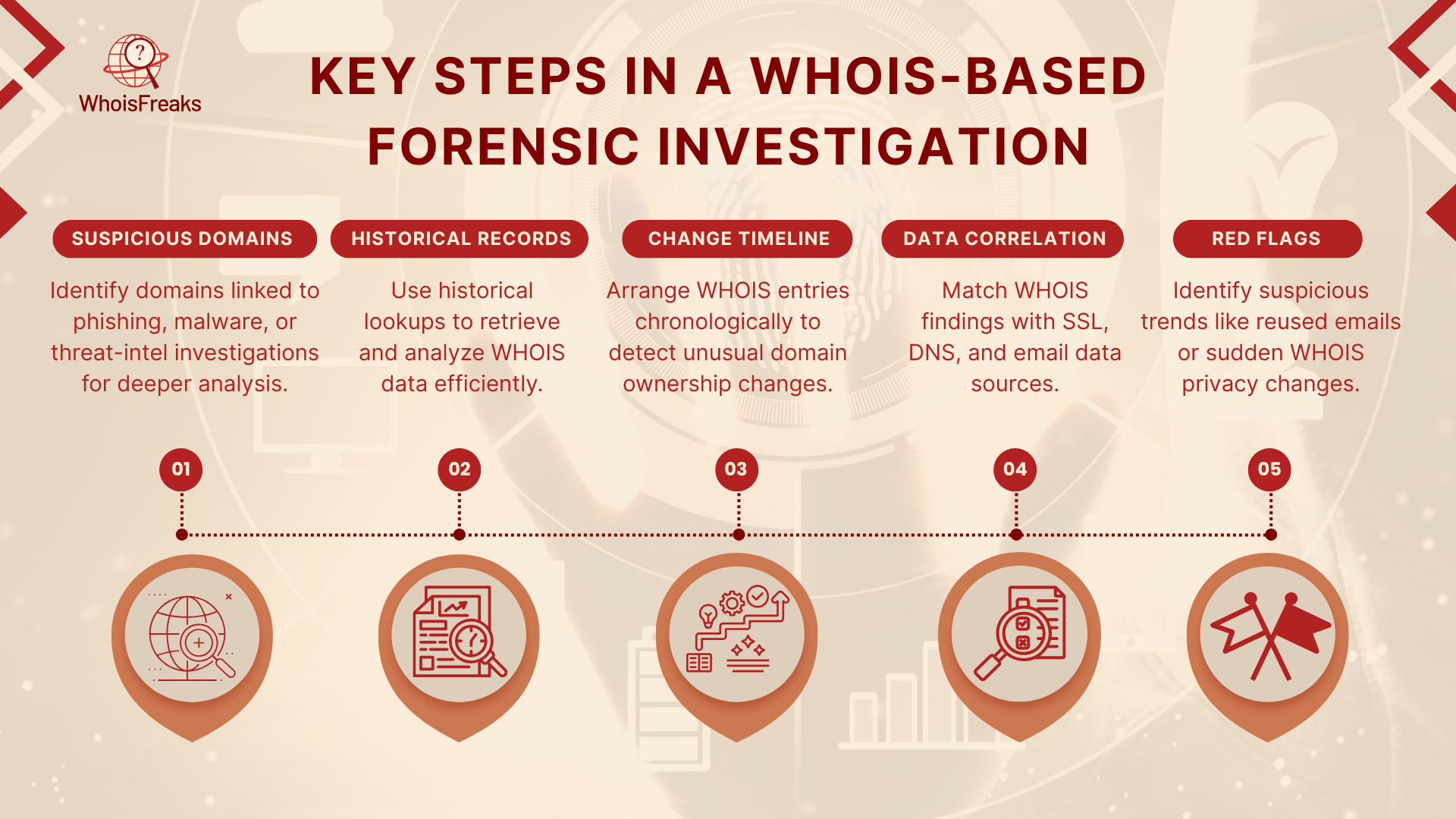
Start by using one or more domain names that you believe they are related to cybercrime. These may be discovered as result of phishing e-mail, malware logs, or suggestions within threat-intel gives. If you want to continue filling out your list, you can use a Reverse WHOIS Lookup at any known registrant email or name address, especially from threat intelligence platforms to discover all the domains associated with that identificatory.
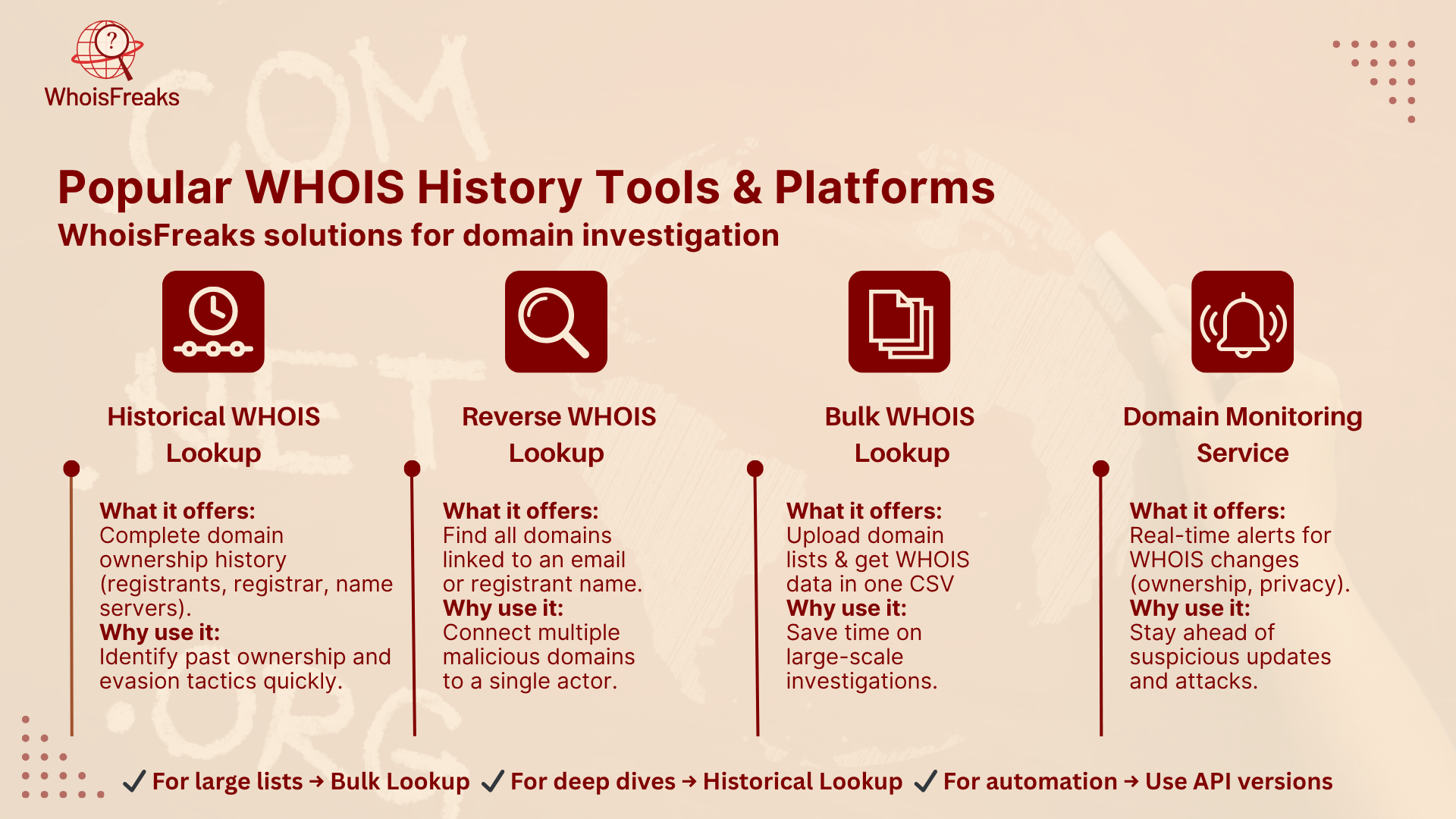
Use the Historical WHOIS Lookup on WhoisFreaks to analyze the WHOIS history data to retrieve WHOIS data for domain names. If you’re working with dozens of domains (for example, an entire phishing cluster), speed up this step with the Bulk WHOIS Lookup, which delivers all records in one CSV.
Arrange the WHOIS entries in a chronological way. Record when the name of registrants, email addresses, registrar, or name servers changed. Compare these changes alongside information found on Historical Lookup and you will be able to identify trends or unexpected changes that indicate evasion.
Match your WHOIS timeline against additional sources for effective incident response:
Look for suspicious signs in your combined dataset:
Here are the go-to specialized software features of WhoisFreaks for digging up WHOIS history and streamlining domain forensics:
One of the small banks in Europe reported their customers receiving emails that appeared as formal log in messages but containing links to secure-bank-login[.]xyz. These are the steps on how you can utilize WhoisFreaks tools to identify the entire phishing network:
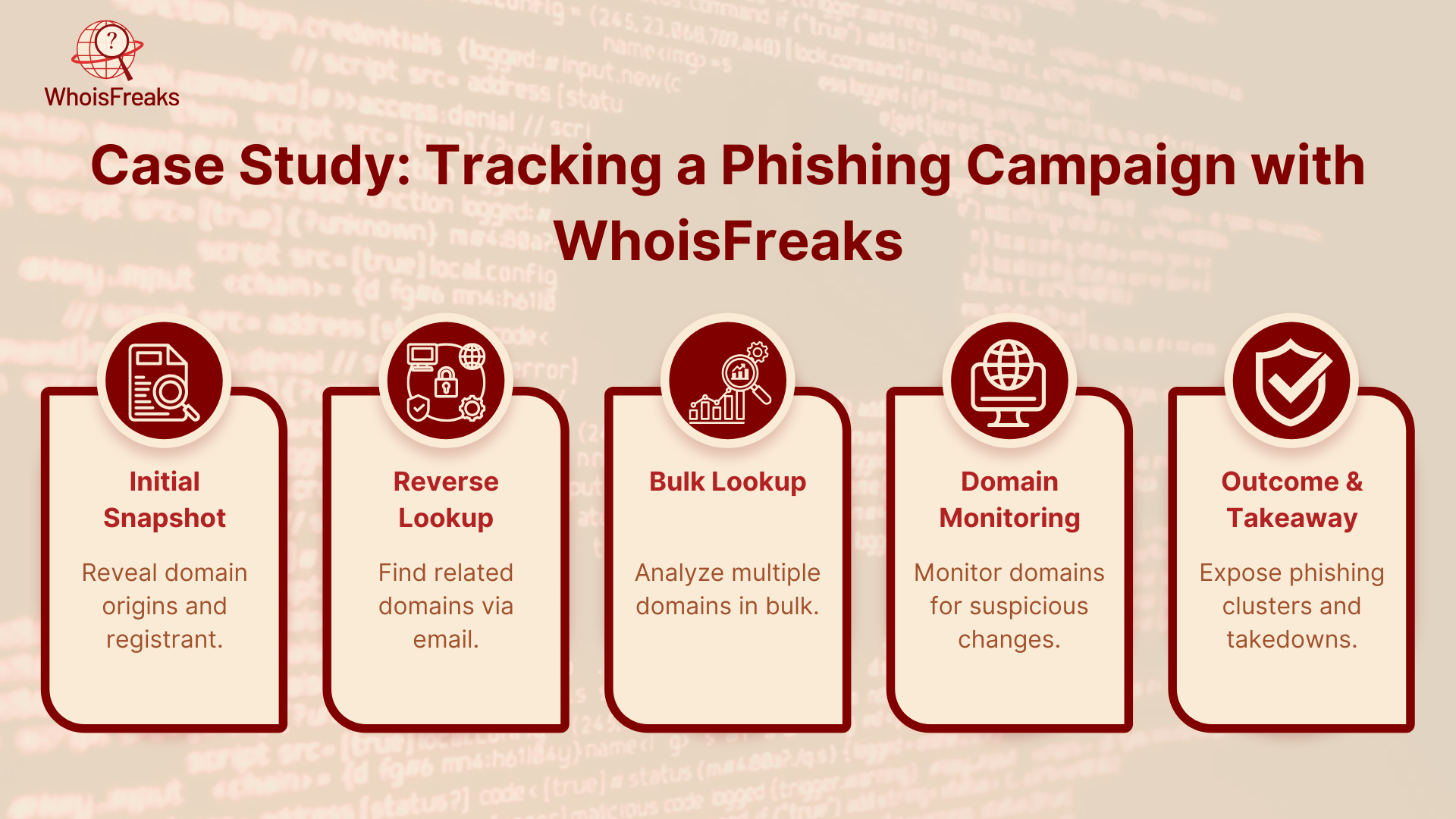
The case demonstrates the benefits of applying Historical WHOIS, Reverse WHOIS, Bulk Lookup, and Domain Monitoring as implemented by WhoisFreaks to your criminal investigations process to reveal the extent to which an attack managed by phishers has occurred and allowed you to stay ahead of the criminals.
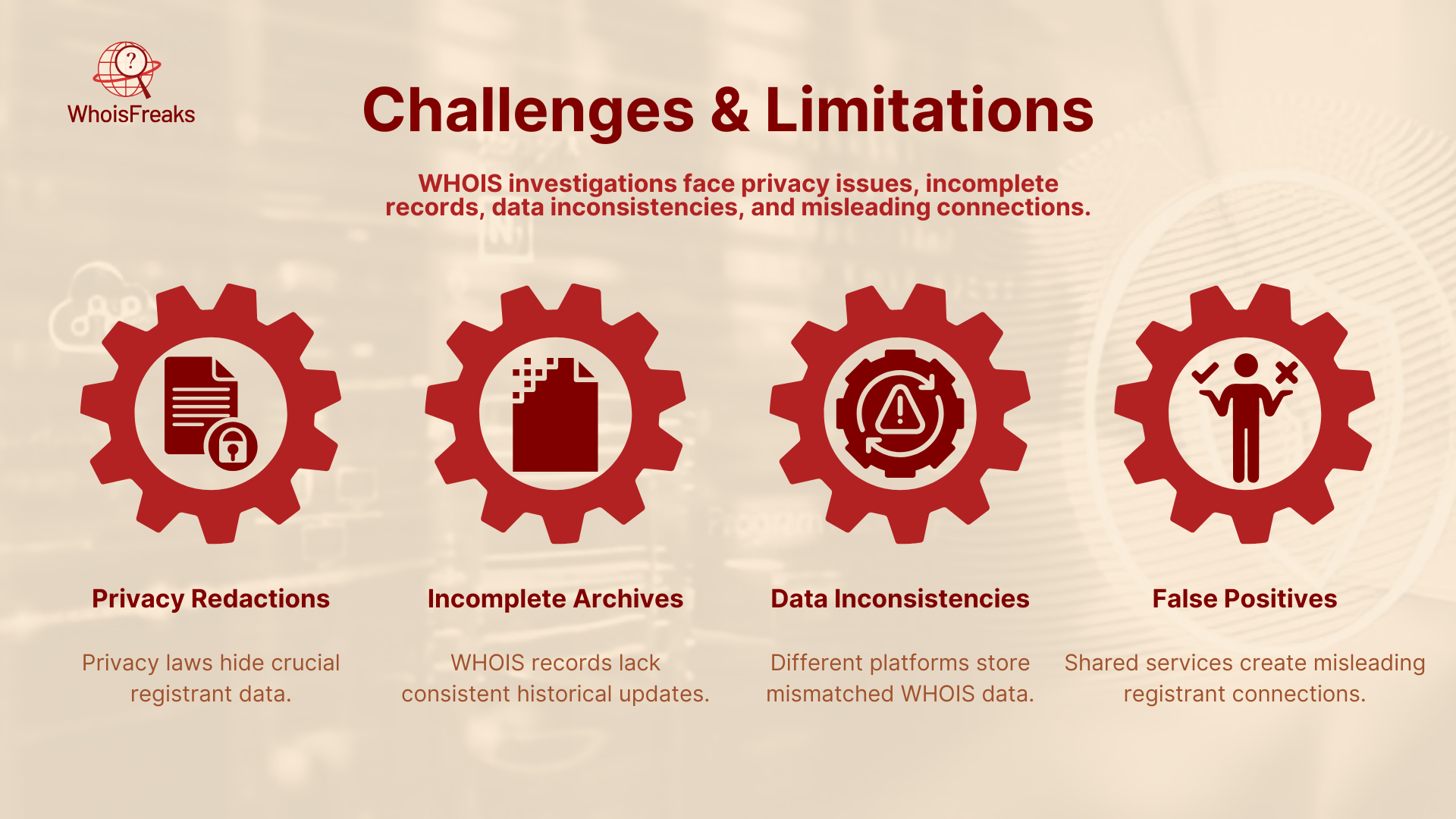
Regulations, such as GDPR and other privacy laws, tend to put a strain on registrars to conceal or censor actual registrant information in the modern-day and age. It implies that up-to-date WHOIS lookups might be practically empty, and you will have to rely on historical snapshots that in turn might be partially masked.
Services do not track all the changes. Not all providers of WHOIS-history provide snapshots daily or even weekly and monthly. You may also miss a vital ownership transfer or name-server change by twice-updating your cybercriminal with snapshots.
slightly varying data formats or retention durations can be stored in different WHOIS-history platforms. One of the services may have a complete archive of six years where another one can only reach back two years. Additional complexity is due to cross-referencing between providers.
Lawful companies do this, and they may all be using the same privacy-proxy / registrar, and your analysis may give “shared” registrant data. You will have to sieve the harmless intersections to avoid going after innocent territories.
WHOIS history is a powerful lens for uncovering the hidden trails of cybercriminals. By digging into past registrant details during digital investigations with tools like Historical WHOIS Lookup, linking domains via Reverse WHOIS Lookup, speeding through large datasets with Bulk WHOIS Lookup, and staying ahead with Domain Monitoring, you can transform a single suspicious URL into a mapped network of malicious sites. These insights help you spot evasion tactics, connect disparate campaigns, and build rock-solid reports for takedown requests or legal action.
Head to WhoisFreaks.com and run your first Historical WHOIS Lookup see exactly who registered a domain, and when.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Learn how subdomain discovery can enhance phishing prevention and protect against spoofing campaigns. Read the article for practical strategies.
12 min read